Seax Security recognises the maxim if you stand still you’re in danger of getting left behind.
As the nature of threat has evolved, so too has our methodology and approach. By walking in the shoes of those who threaten our interests and replicating their attack planning process, we are constantly adapting to meet the changing threat picture.
This process is known as the Adversarial Planning Model ®
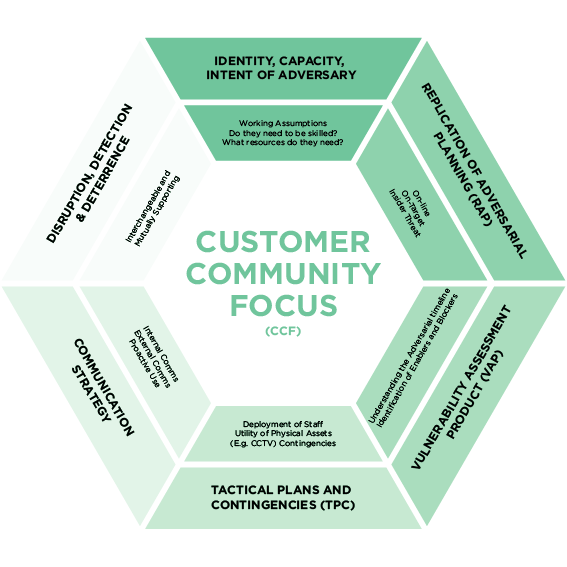
This flexible methodology to understanding threats supports bespoke services
- Hostage and Extortion policy review
- Counter terrorism security reviews (supported by hostile reconnaissance Replication).
- On line vulnerability to social engineering assessment of staff and assets
- Assessment of your organisational security culture
- Development of security minded communication strategy and supporting tactical plans, to mitigate internal and external threats.
- Review of emergency plans and policies
Privacy & Cookies: This site uses cookies. By continuing to use this website, you agree to their use. To find out more, including how to control cookies, see here: Cookie Policy

